Hardware Security in IoT: Hardening your devices 💪🏻
Hardware security matters as much as software security in any IoT devices. This blog explores different modes of attacks and provides few guideline which can help design more secure products.

Let's go through an IoT product security checklist:
- You are using device certificates to authenticate and TLS 1.3 to do that fast. (Read this blog to know more)
- Device interactions like control panels or web interfaces are secured by passwords to avoid unauthorized configuration changes.
- You have hardened your device against physical attacks and limited its reach to other sub-systems of your product: Wait! What? Is that even a thing?
Turns out that is one of the most important things you need to do to keep your devices secure. Let me tell you why, it can get really scary if someone hacks into your device. Not believing me? Watch this video:
Now, you'll say it's 9 years ago.. but all it takes is a single zero-day vulnerability to repeat itself. And sometimes it can be even in ways you haven't even thought of. For example, here is a study published in 2020 that can control your home assistant devices remotely through a laser-based signal injection in MEMS Microphones found on such devices. Imagine someone points a DIY laser pointer at your voice assistant device from the window and says "Open the main door", well you can imagine. Go on, I suggest you read it to get an idea that it's not always just online cyberattacks that need to be taken care of.
Another type of attack can be physical, sometimes called hardware trojans. Want to have a good idea of what hardware trojans are? Here is another research paper. The essence of that paper is shown here:
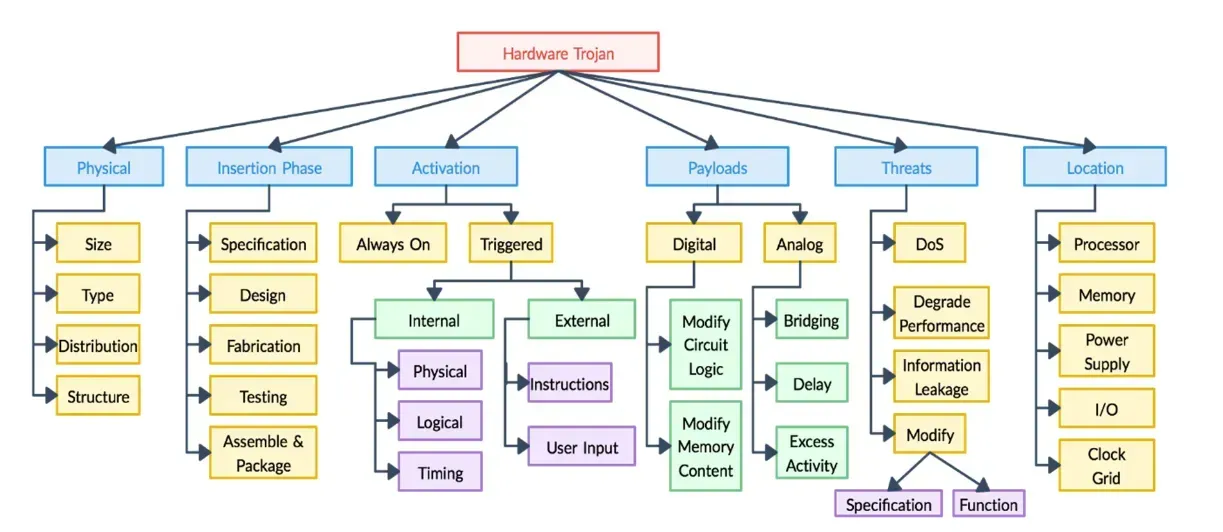
The purpose behind showing you all these attacks is to broaden your security mindset. Most engineers just think about TLS/SSL or encrypting their firmware at most and then feel that nobody can get into their product and it's safe; while reality can be miles away. And remember, it is quite possible that the goal is not to break your device but to gain access to the main network through your device.
Now, as I always say: no system is safe, given enough resources and time any system can be broken or hacked. So your job as a product designer is to make sure that either time or resources required are so high compared to potential gain that it simply doesn't make sense to pursue it.
Here are a few ways you can avoid such attacks.
Harden Credentials Storage
Your devices may have multiple security credentials, it can be certificate private keys, WiFi SSID and Passwords etc. You can secure these credentials by storing them in dedicated security ICs. These ICs are designed in a way that information can not be extracted out of it without proper authentication. Many MCUs today provide encrypted storage.
TPM chips are ideal for storing device certificates and can provide significant security against probing attacks if used correctly, as a private key is generated inside the chip and never leaves the chip.
Limit Port Access
Most products have some sort of ports open, either as a part of product functionality or for manufacturability. It can be JTAG ports or UART ports to load and test firmware. Either, remove such ports physically or disable them through firmware. Most MCUs have fuses to disable JTAG ports permanently.
Verify Supply Chain
Verify that you are receiving your components from a verified distributor. Sometimes vulnerability is injected at the time of manufacturing through clones of certain components, say MCU or security chips. That's why almost all modern MCUs have a unique ID that can be verified with the manufacturer and all TPM chips have a unique certificate burned permanently into it so that it can be verified to check whether it is genuine or not.
Provide Tamper Proofing and Tamper Evident features
Incorporate tamper proofing and Tamper evident measures into your product. Tamper-proofing measures make it hard to tamper with the device. For example, covering the main MCU with hard epoxy makes it harder to directly access MCU pins.
Tamper-evident features, on the other hand, provide evidence that the device is tampered with in some manner. It can be active also, for example, many TPM chips provide chassis intrusion pins. If someone breaks into the device chassis, the chip will immediately erase all secure information and that device becomes useless for the attacker.
Use Zero-Trust Strategy
Zero-trust is a security strategy that assumes that no device, user or network can be trusted. And you design security practices navigating through this assumption.
Finally, Limit your device's impact.
As I said, all it takes is a single vulnerability. Design your product in a way that isolates critical systems and if an attacker finds a way in, there's not much which can be done. For example, the Infotainment system does not need access to the Engine Control Unit(ECU) in a car, hence keep them separate or at least connect them with some security mechanism in between.
Conclusion
It is not always cyberattacks that can compromise a device. Hence, a product should be designed by keeping all these things in mind.
When you have so much to take care of, Anedya makes it a lot easier by taking care of all cloud security concerns. 😁
Happy Designing!